
Potential Earnings in the Cybersecurity Field
Explore potential earnings in cybersecurity. Learn about entry-level salaries, top-paying roles, and how factors like skills, certifications, and location impact your earning potential.
Expert insights on AI agent identity management, enterprise security, compliance, and governance. Learn how to scale AI operations securely with AuthFyre's thought leadership on IAM, Zero Trust, and AI workforce management.

Explore potential earnings in cybersecurity. Learn about entry-level salaries, top-paying roles, and how factors like skills, certifications, and location impact your earning potential.

Discover essential cybersecurity best practices for AI agent identity management and enterprise software. Learn to protect your systems with strong authentication, regular updates, and proactive threat detection.

Understand the confused deputy problem in cybersecurity, its implications for AI agent identity management, and how to mitigate risks in enterprise software. Learn about real-world examples and practical solutions.

Learn essential identity management concepts for AI agents, including authentication, authorization, governance, and compliance. Securely integrate AI into your enterprise.

Understand essential cybersecurity concepts for enterprise software and AI agent identity management. Learn about threat detection, access control, and data encryption.
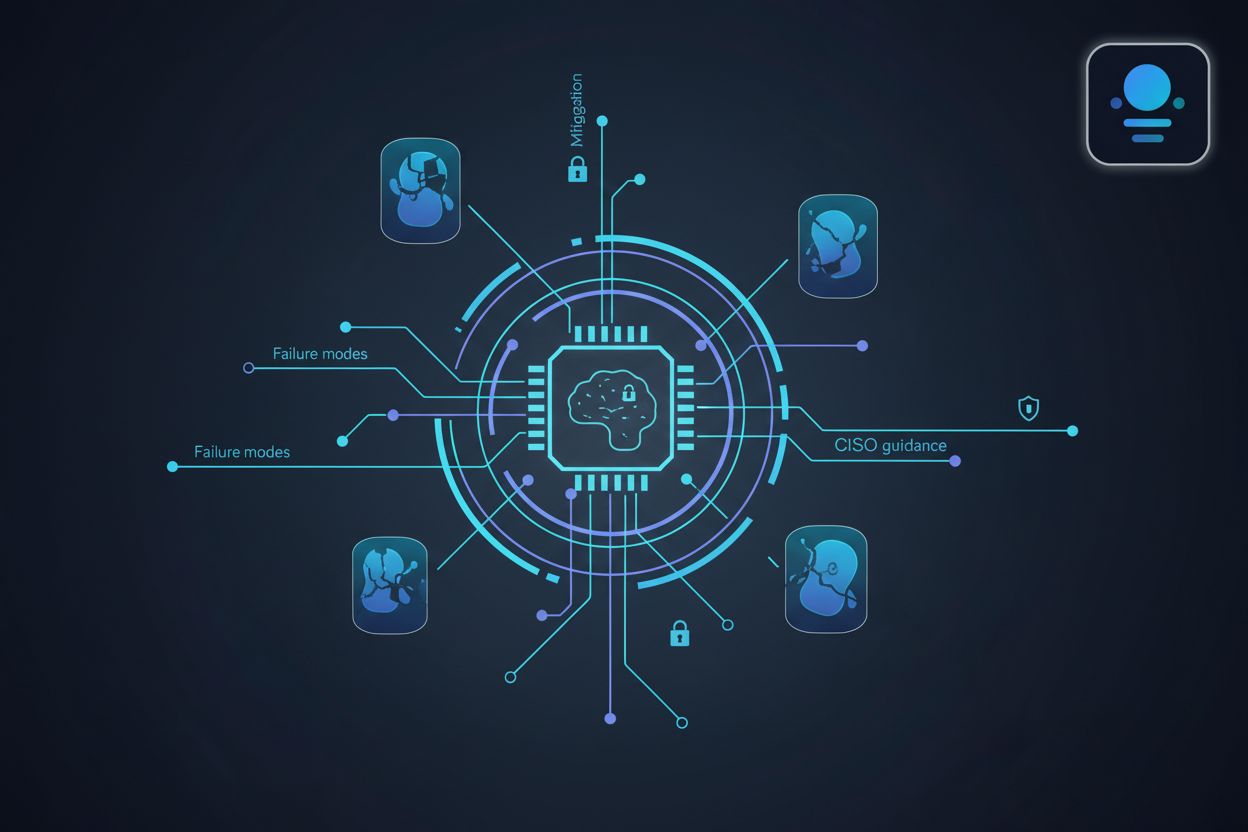
A comprehensive guide for CISOs on identifying and mitigating AI agent identity failure modes. Learn to secure your enterprise from rogue access and compromised AI agent credentials.

Explore cybersecurity fundamentals crucial for AI agent identity management and enterprise software. Learn about access control, encryption, and vulnerability management to safeguard your digital assets.

Explore how the Confused Deputy Problem is resurfacing in cybersecurity with AI agents. Understand risks & mitigation for enterprise software.

Explore the security challenges and governance strategies for agentic AI. Learn how to secure autonomous agents in enterprise environments with identity management and access control best practices.