
Identifying the 7 Types of Cybersecurity Threats
Learn about the 7 major cybersecurity threats targeting AI agent systems. Understand risks like malware, ransomware, phishing, and AI poisoning, plus mitigation strategies.
Expert insights on AI agent identity management, enterprise security, compliance, and governance. Learn how to scale AI operations securely with AuthFyre's thought leadership on IAM, Zero Trust, and AI workforce management.

Learn about the 7 major cybersecurity threats targeting AI agent systems. Understand risks like malware, ransomware, phishing, and AI poisoning, plus mitigation strategies.

Explore Content Disarm and Reconstruction (CDR) as a robust cybersecurity solution for AI agent identity management and enterprise software. Learn how CDR protects against file-based attacks.

A practical guide for CISOs on governing AI agents, covering identity management, compliance, risk mitigation, and security best practices.

Explore the landscape of hardware attacks in cybersecurity, including types, prevention, and emerging trends. Learn how to protect your enterprise from these threats.
Explore the evolving landscape of Identity Management for Agentic AI. Learn about dynamic frameworks, zero trust, security strategies, and more.

Learn how the Confused Deputy Problem impacts AI agent security. Discover vulnerabilities and mitigation strategies for enterprise software.
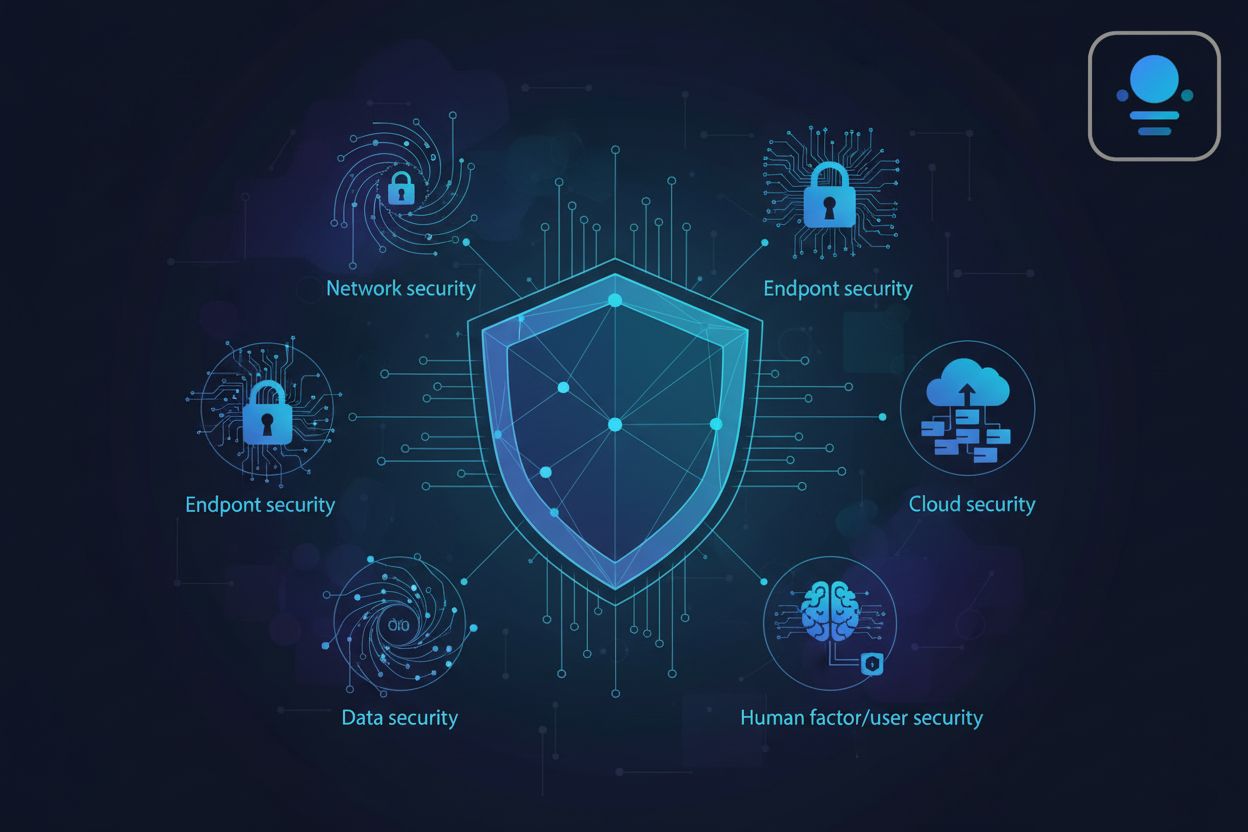
Explore cybersecurity: its definition, importance, various types (network, cloud, endpoint security), key threats, and best practices for protecting your organization.

Learn how to prevent cross-service confused deputy attacks in your organization's cybersecurity strategy, especially with AI agent identity management. Practical guide for IT security professionals.

Explore the Confused Deputy Problem in cybersecurity: understand its risks, real-world scenarios, and how to mitigate it using modern PAM solutions and least privilege strategies.