
Insights into Continuous Threat Exposure Management
Learn how Continuous Threat Exposure Management (CTEM) secures enterprise software and ai agent identity management against modern cyber threats.
Expert insights on AI agent identity management, enterprise security, compliance, and governance. Learn how to scale AI operations securely with AuthFyre's thought leadership on IAM, Zero Trust, and AI workforce management.

Learn how Continuous Threat Exposure Management (CTEM) secures enterprise software and ai agent identity management against modern cyber threats.

Discover common scenarios of hardware security failures and how they impact AI agent identity management and enterprise cybersecurity strategies.

Explore common questions about cybersecurity focusing on AI agent identity management, enterprise software security, and identity governance for IT pros.

Detailed guide on the effectiveness of Control-Flow Integrity (CFI) for cybersecurity. Learn about CFB attacks, shadow stacks, and ai agent identity management.
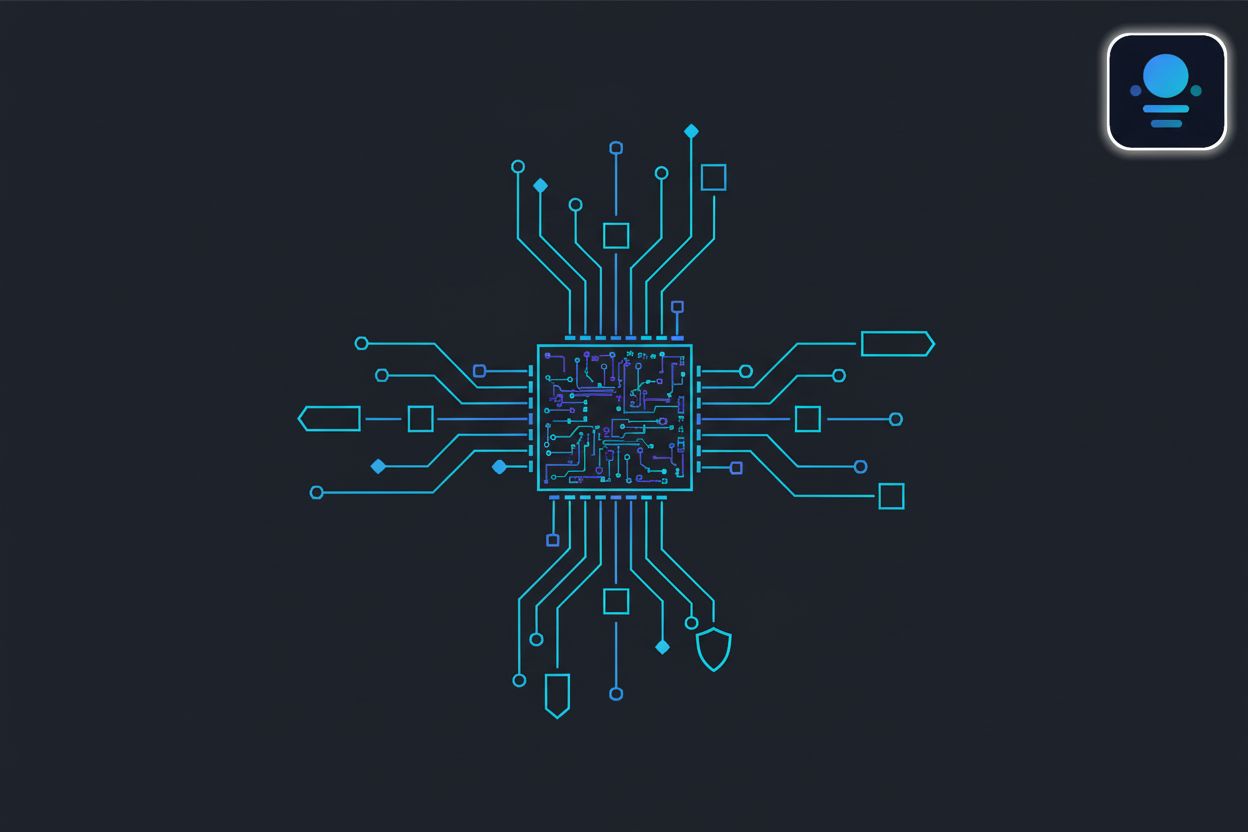
Explore how Control-Flow Integrity (CFI) protects enterprise software and AI agent identity management from memory exploits and execution hijacking.

Deep dive into Control-Flow Integrity (CFI) for cybersecurity R&D. Learn how CFI protects AI agent identity management and enterprise software from exploits.
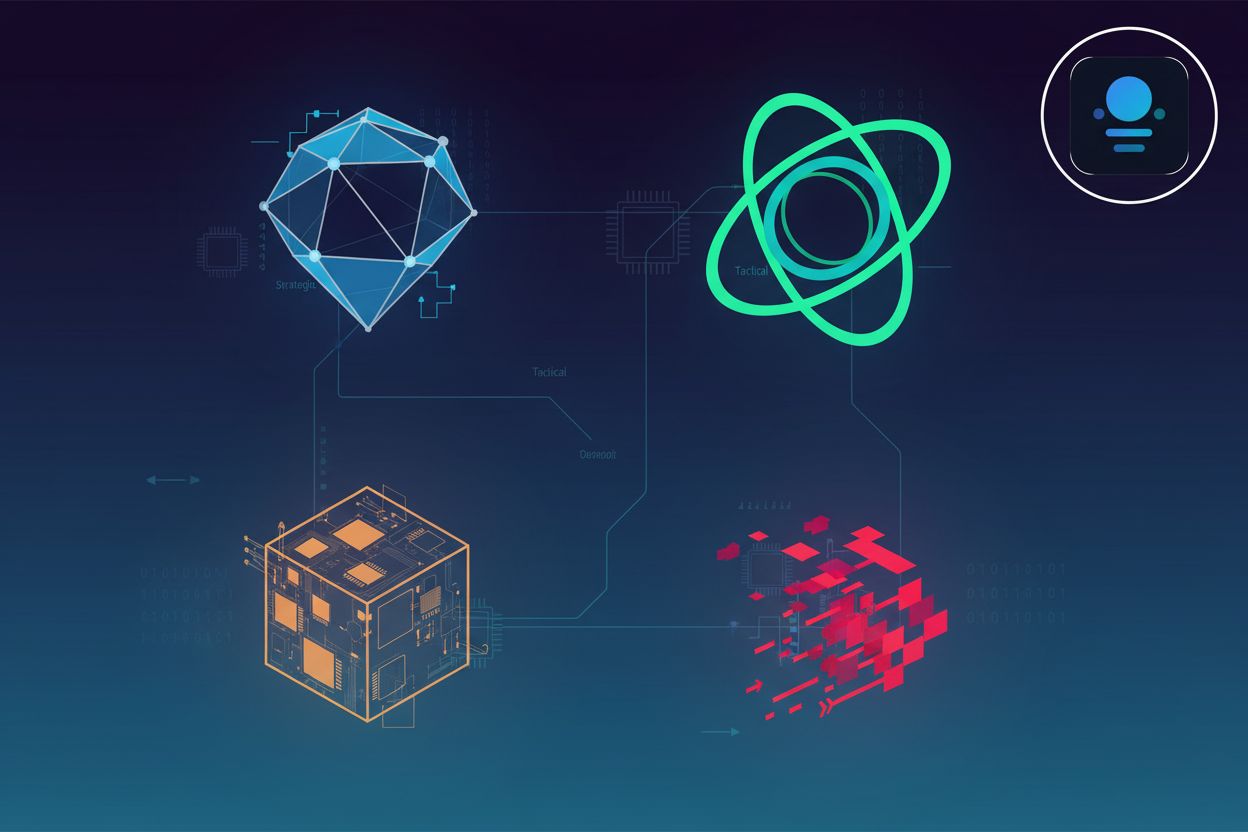
Learn about the four types of cyber threat intelligence—strategic, tactical, operational, and technical—and how they apply to ai agent identity management and enterprise software security.

Learn how to manage ai agent identity management and cybersecurity in the enterprise. Explore identity governance and workforce management for autonomous agents.

Learn how to implement Control-Flow Integrity (CFI) to secure modern enterprise software and AI agent identity systems against memory safety attacks.