
Exploring Continuous Threat Exposure Management
Discover how adopting Continuous Threat Exposure Management (CTEM) can revolutionize your cybersecurity strategy. Learn about its lifecycle, components, and benefits for AI agent identity management.
Expert insights on AI agent identity management, enterprise security, compliance, and governance. Learn how to scale AI operations securely with AuthFyre's thought leadership on IAM, Zero Trust, and AI workforce management.

Discover how adopting Continuous Threat Exposure Management (CTEM) can revolutionize your cybersecurity strategy. Learn about its lifecycle, components, and benefits for AI agent identity management.

Explore a 24-hour honeypot experiment, analyzing attack patterns and vulnerabilities to improve cybersecurity for AI agent environments. Learn practical defense strategies.
Learn about Content Disarm and Reconstruction (CDR) and how it protects AI agent identity management and enterprise software from sophisticated cyber threats. Explore its implementation and benefits.

Explore Content Disarm and Reconstruction (CDR) software, its benefits, how it works, and its role in protecting enterprise systems from file-based cyber threats. Learn about CDR's evolution and implementation.
Explore Content Disarm and Reconstruction (CDR) and its role in cybersecurity. Learn how it protects against file-based threats in AI agent identity management and enterprise software.

Learn about Content Disarm and Reconstruction (CDR) and how it protects your enterprise from file-based threats, especially in AI agent identity management. Discover implementation strategies and best practices.
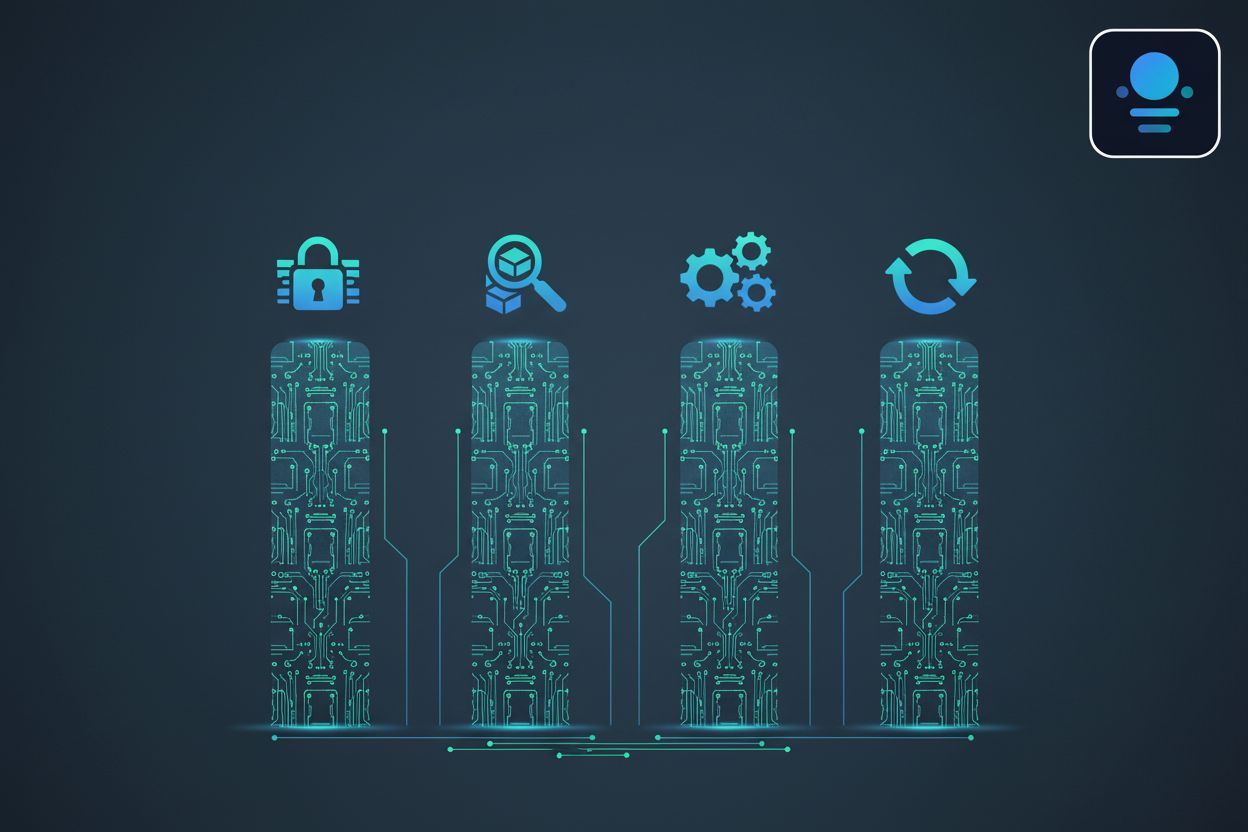
Explore the four pillars of cybersecurity in the context of AI Agent Identity Management, Cybersecurity, Enterprise Software. Learn how to build a robust security strategy.
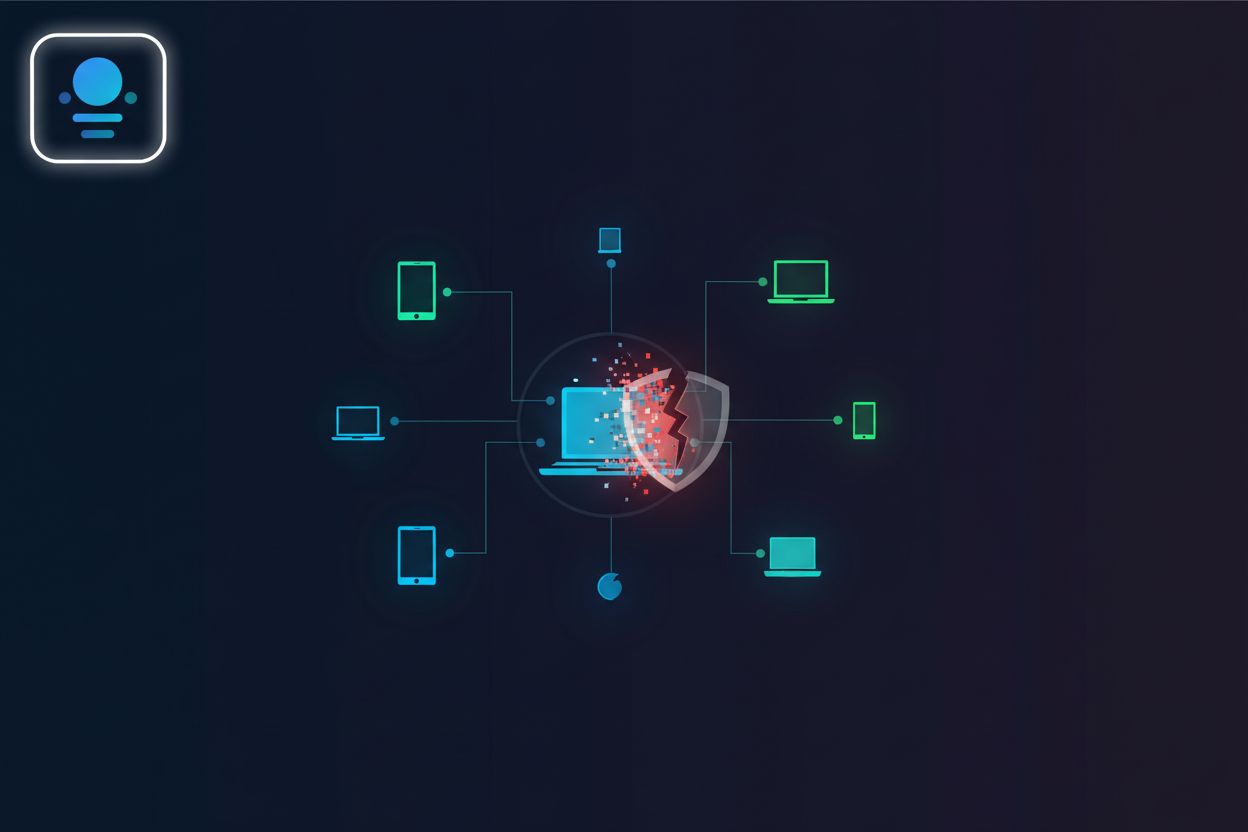
Learn how to identify, understand the risks, and mitigate threats from compromised devices in your enterprise. Explore AI-driven solutions for enhanced cybersecurity.

Explore Content Threat Removal (CTR) in cybersecurity, contrasting it with traditional methods. Understand its applications, limitations, and role in modern enterprise security.